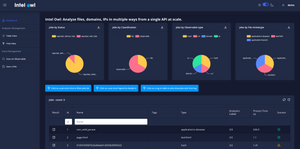
Both Cortex and IntelOwl are awesome tools for observable analysis, I wanted to learn a bit about both of them and what better way to do that than trying both tools and writing a comparison of them?
I rarely get the chance to compare two different awesome tools and write detailed posts about them, but I am off work now, and I have few free hours to spare so here is an unbiased, somewhat detailed comparison of Cortex and IntelOwl.
Disclaimer: Both platforms are amazing, both are open source, and both have outstanding teams behind them, this post is merely to outline the features of both tools and give you a better idea on what to expect when picking one or the other.
Introduction
Both Cortex and IntelOwl are Observable Analysis tools which are tools used by security professionals (specially incident handlers) to obtain information about a suspicious observable (e.g. domain details, IP health information, file type, static analysis of a file, ...).
Cortex
Cortex tries to solve a common problem frequently encountered by SOCs, CSIRTs and security researchers in the course of threat intelligence, digital forensics and incident response: how to analyze observables they have collected, at scale, by querying a single tool instead of several?
Cortex, an open source and free software, has been created by TheHive Project for this very purpose. Observables, such as IP and email addresses, URLs, domain names, files or hashes, can be analyzed one by one or in bulk mode using a Web interface. Analysts can also automate these operations thanks to the Cortex REST API. (source)
IntelOwl
Intel Owl is an Open Source Intelligence, or OSINT solution to get threat intelligence data about a specific file, an IP or a domain from a single API at scale. It integrates a number of analyzers available online and is for everyone who needs a single point to query for info about a specific file or observable. (source)
Comparison
Ease of Installation
Starting with a clean VPS, it took me seven minutes to install an instance of IntelOwl, granted a not-so-ready instance but an instance nonetheless. The instance had most of the analysers enabled and configuring the more advanced ones is quite straightforward once you have read the documentation.
I followed Arnaud's awesome guide on installing The Hive & Cortex, I only needed Cortex, so I only install that part. It took me about 15 minutes to get a testing instance up and running. No analysers are configured by default but enabling them is straightforward.
User Interface
Both tools have well-made user interfaces, IntelOwl does look a bit more modern due to the colours but when it comes to functionally and ease of accessing it, both projects are pretty much on par with each other.
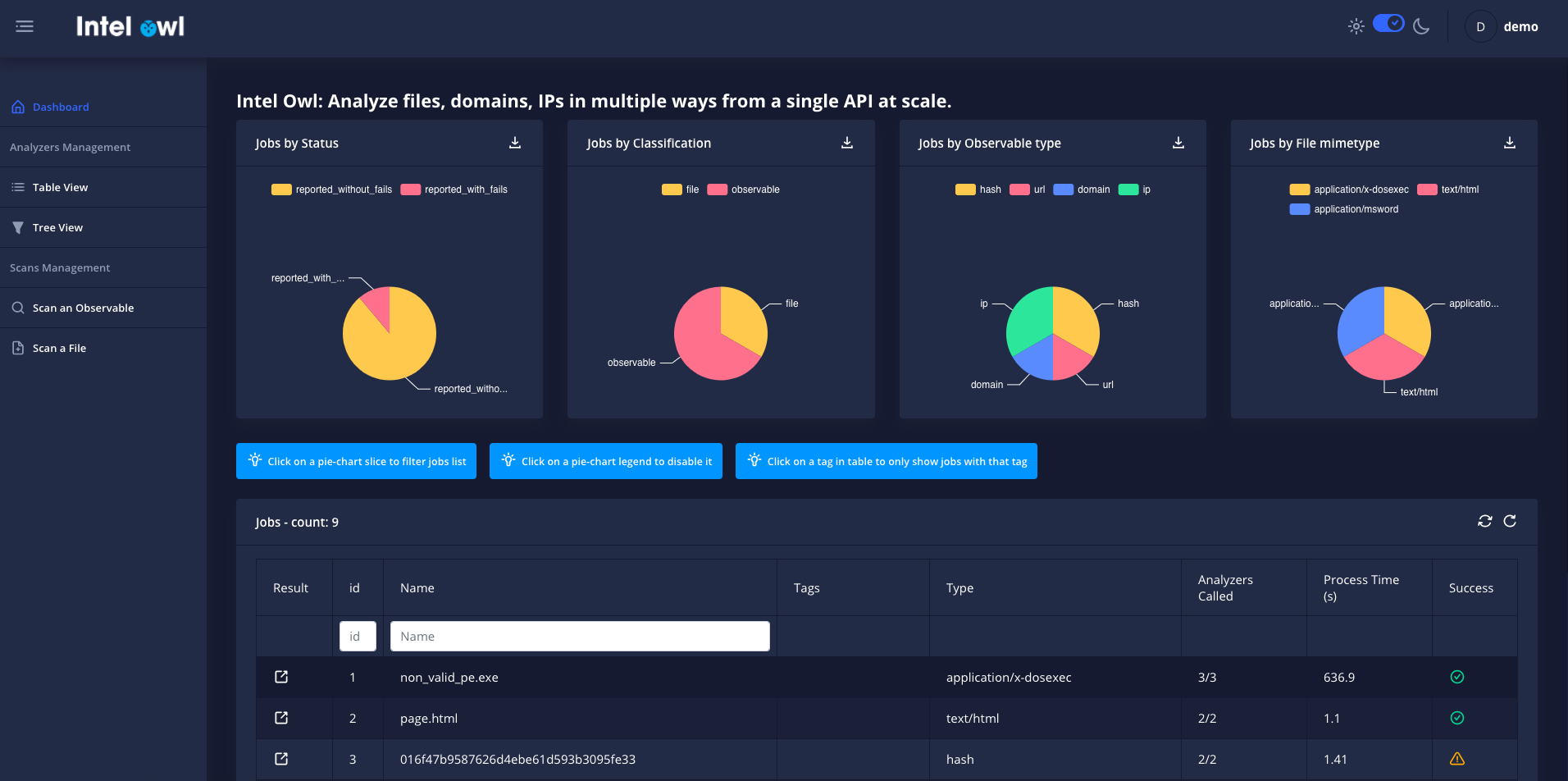
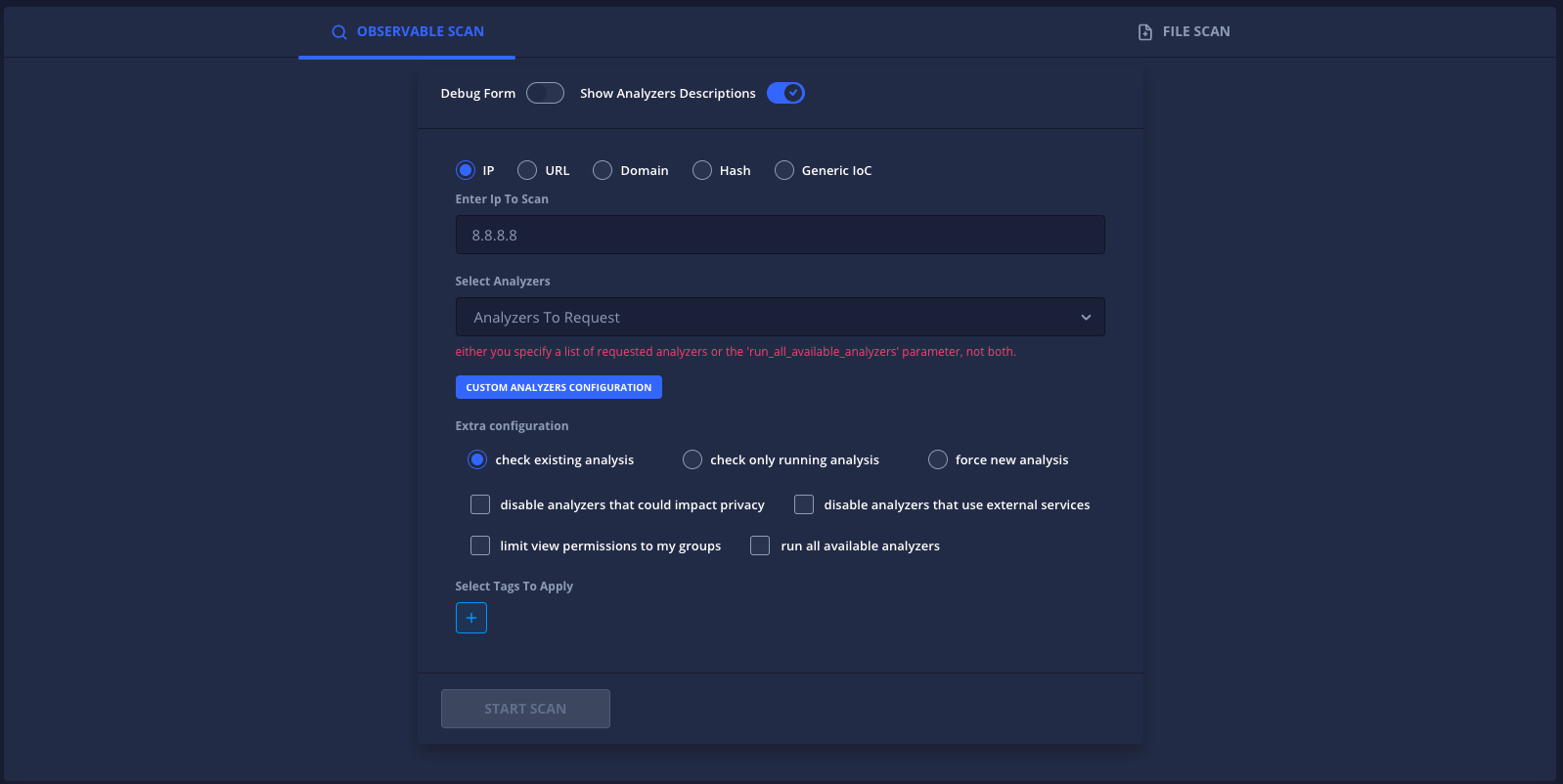
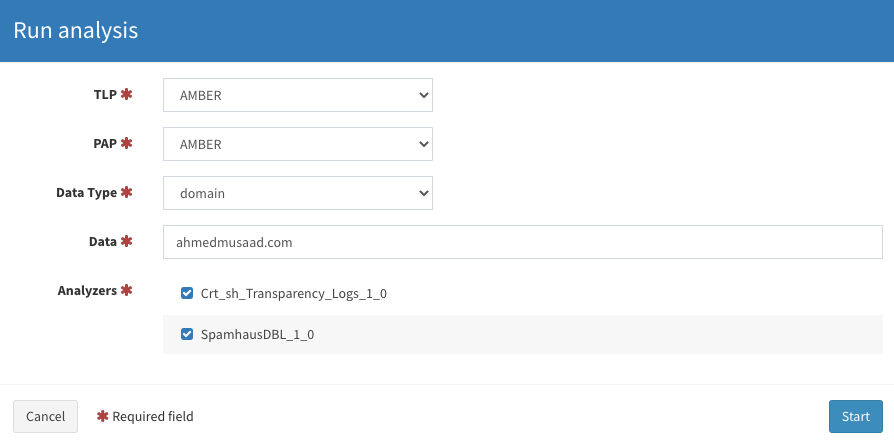
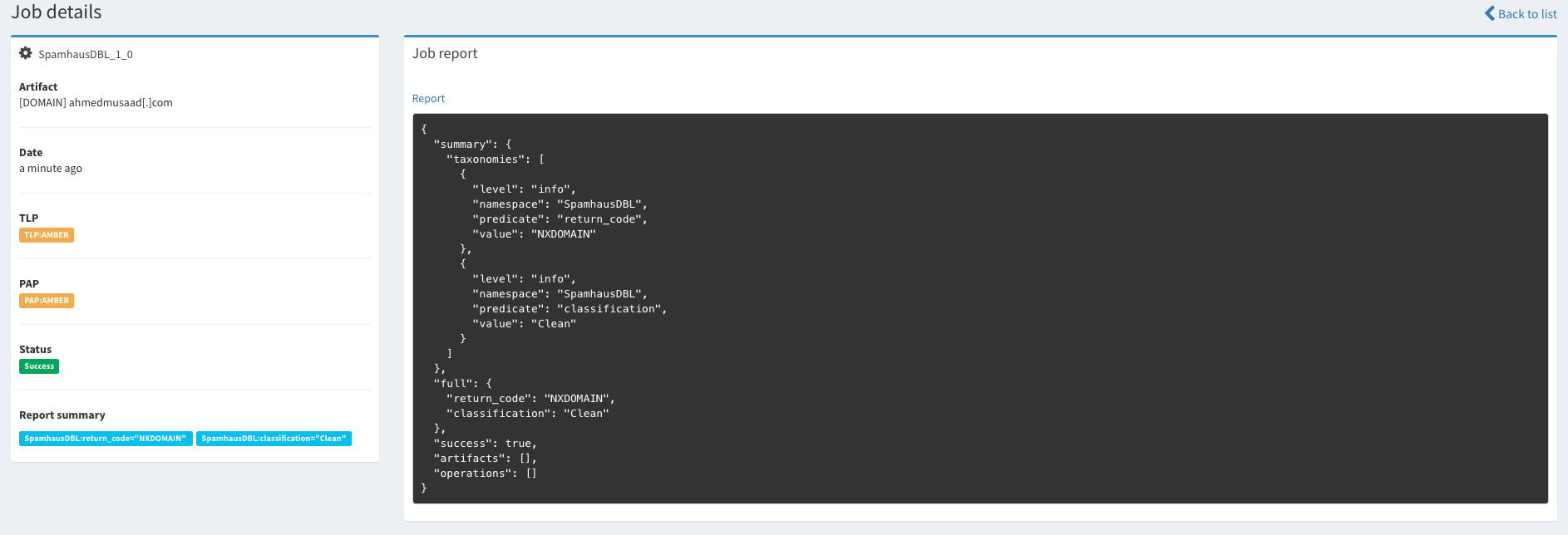
Administration & Configuration
IntelOwl exposes little administration options through the GUI which makes the administration experiences a bit less streamlined. Most configurations are stored in configuration files which are easy to edit and work with once you read the documentation.
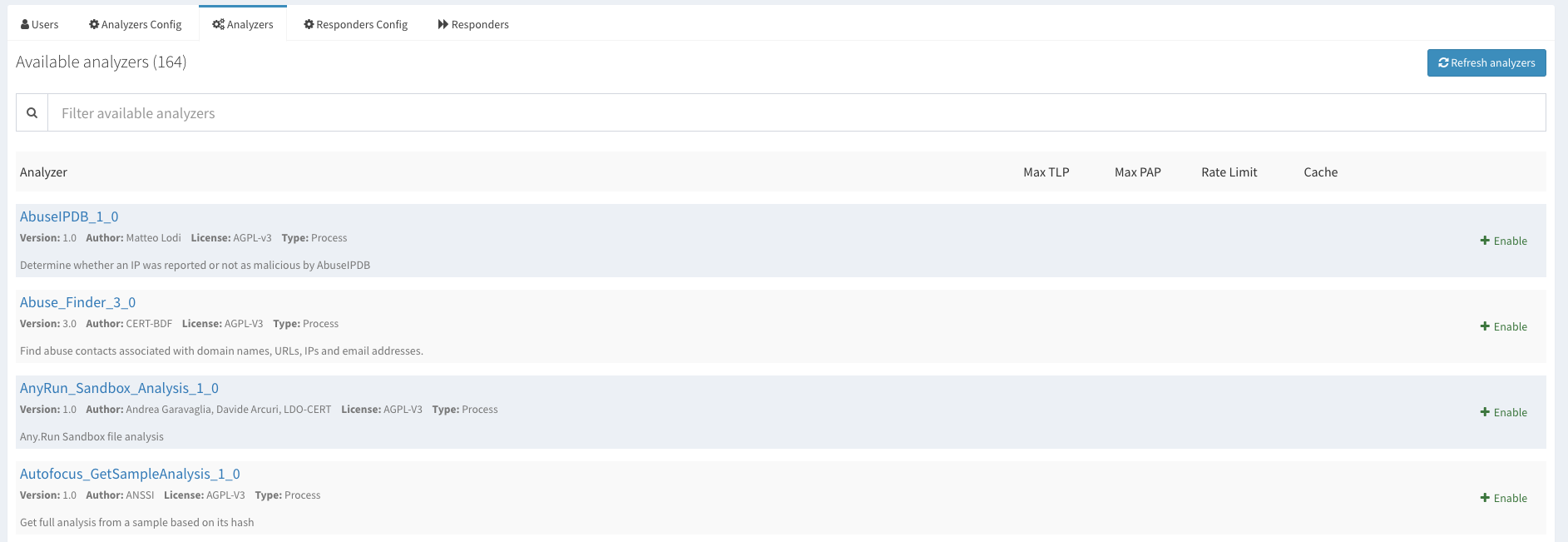
Cortex exposes more of its administration options through the web interface including configuring organizations, users, analysers, responders and more. This makes the administration experience better and more streamlined.
Command Line Clients
Both tools have CLI clients which allows users to interact with the platforms and build more complex CLI tools that make use of these clients. IntelOwl's client is pyintelowl, Cortex's is Cortex4py. IntelOwl's team created a recording for how to use their command line client, check it out.
Supported Analysers
Both platforms supported a wide range of analysers, and both are quite extendible if you wish to create your own custom analyser. You can find the list of supported analysers in the following links (Cortex analysers), (IntelOwl analysers).
Counting all readily available analysers (paid, free, and those with special requirements), Cortex has a total of 105 while IntelOwl has 127 analysers. Both have great coverage for various types of analysis tasks that you might need to perform during an investigation or while doing some research.
Maturity
The maturity of an open source project is a bit tricky to measure in a fair and accurate way, but I will try my best to give you some facts, and you can use that information however you like.
- The first release of Cortex was on Feb 1, 2017 and since then 25+ releases were published. IntelOwl first release was published on Jan 9, 2020 and since then 23+ releases were published.
- Cortex has 11 contributors, IntelOwl has 21.
- Both projects are actively developed and maintained, if you take a look at the GitHub repo, both had commits in the last month.
- Both projects are licensed under AGPL-3.0 Licence.
Development
If you are considering contributing to either projects or building upon them, then which technologies are used to develop the tools would most likely matter to you. Cortex is developed using Scala, on the other hand, IntelOwl is built using Python.
Conclusion
Both Cortex and IntelOwl are awesome tools that can be of extreme benefit to any security professional who's interested in observable analysis or works in incident handling. Check them out, support their creators, and if you have some time to spare, contribute to the projects.
Links
- TheHive-Project/Cortex: Cortex: a Powerful Observable Analysis and Active Response Engine (github.com)
- intelowlproject/IntelOwl: Intel Owl: analyze files, domains, IPs in multiple ways from a single API at scale (github.com)
- intelowlproject/pyintelowl: Robust Python SDK and Command Line Client for interacting with IntelOwl's API. (github.com)
- TheHive-Project/Cortex4py: Python API Client for Cortex (github.com)
- intelowlproject/pyintelowl: Robust Python SDK and Command Line Client for interacting with IntelOwl's API. (github.com)
- Open Source SIRP with Elasticsearch and TheHive - Part 4 - TheHive & Cortex | Arnaud Loos