The second day of Hack.lu is often the longest since it includes the social events at the end which can go on well into the night. This day was no different, it started early in the morning and ended just before ten o’clock. I was exhausted when I arrived back at my accommodation but it was totally worth it.
Credit: All videos are recorded and uploaded by the amazing @cooper. You can find the full list on his website: https://administraitor.video/edition/Hack.lu/2019
Sensor & Logic Attack Surface of Driverless Vehicles
I was a bit late to the first talk, I blame that on public transportation in Luxembourg city and all the construction work being done near my accommodation. The talk was delivered by Zoz, a robotics interface designer and rapid prototyping specialist. He presented a great talk on driverless cars, the systems that usually used for such cars, and the failure modes and attacks that affect these various systems and their subsystems. Fair to say, I feel seriously concerned about the safety of many car models that are currently on the streets.
Disturbance: on the Sorry State of Cybersecurity and Potential Cures
Next up was Saad Kadhi (@_saadk)who presented a thoughtful talk on “Disturbance: on the Sorry State of Cybersecurity and Potential Cures” which resonated with a lot of those who were in the conference hall and evoked lots of agreeing head nods. He talked about the zoo of information security products, an environment where multiple products live and one that keeps growing every now and then. He pointed out the gross overcomplication of the information security spectrum and the astounding failure from vendors to fulfill their promises. But it’s not all gloomy, he did offer few options that we can use to improve the situation. This talk hit too close to home and hopefully, the reflecting that comes after will lead to some concrete actions that improve the security of our workplaces and ultimately countries.
Leveraging KVM as a debugging platform
The next talk was on using KVM as a debugging platform and to say it was a cool and impressive talk would be an underestimation. Mathieu (@mtarral) presented a quick overview of the current state of debugging APIs in various virtualization stacks. He highlighted the fact KVM is lagging behind other stacks when it comes to debugging APIs. He then presented the project he’s been working on which is an awesome implementation of a debugging API that opens up the possibilities for security researchers concerning debugging various apps and systems while utilizing KVM.
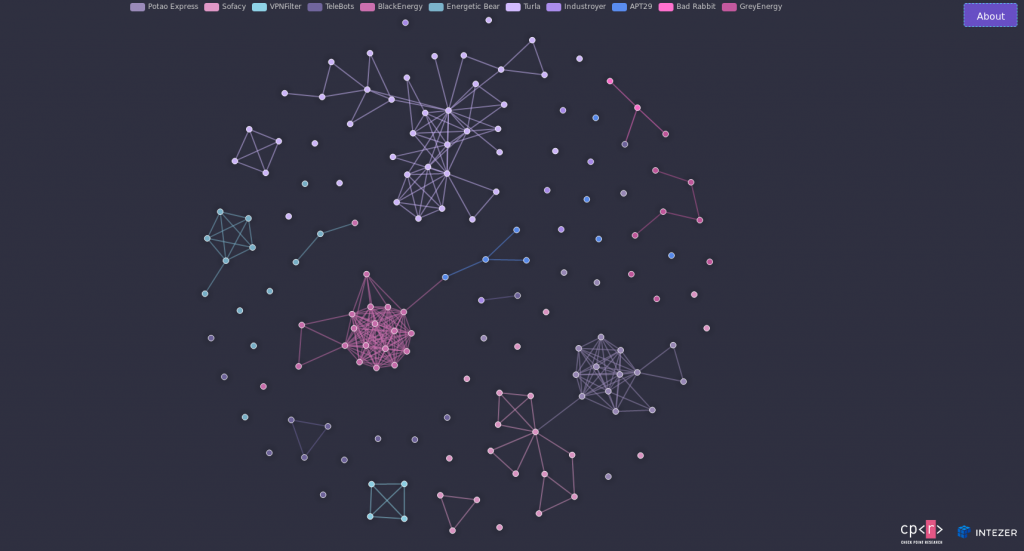
The Red Square – Mapping the connections inside Russia’s APT Ecosystem
This talk was embargoed which means there will be no recording of it but I can give you the gist of it. The researchers (Itay Cohen and Ari Eitan) did a great job in their attempt to collect, classify, and connect various Russian APT families. They presented a brilliant representation of the results of their research and even published a website that can be used to learn more about the Russian APT ecosystem (Link).
Fileless Malware Infection and Linux Process Injection in Linux OS
his talk was given by Hendrik Adrian (@MalwareMustDie) and it was awesome. It was full of useful information that’s vital to incident response teams everywhere. Just take a look at the presentation, the number of pages alone should give you an idea of how comperhensive this presentation was (Link).
Breaks
I have to say this, the lunch and refreshments’ breaks at Hack.lu are amazing. Lots of great food, snacks, drinks, and plenty of coffee. These breaks make the entire experience much more pleasant.
Exploiting bug report systems in the game industry
After lunch, we listened to Andreia Gaita who presented an interesting talk on exploiting bug reporting functions in popular game engines to gain a foothold into game development companies. Her talk presented a unique perspective into a field that’s unknown to me. Her explanation and introduction were clear and easy to follow which made the entire talk a really nice once that taught us good lessons on the security of specialized platforms.
What the log?! So many events, so little time…
Now you must be thinking what’s with all the talks on SoC and logging? It’s a very important topic and it gives a lot of people unprecedented levels of stress. Not to worry, Miriam Wiesner (@MiriamXyra) is here to make our life easier. Her talk addressed the importance of event logs, compliance templates and proper log collection. She presented her tool EventList which helps SoC engineers and architects load a specific compliance profile and get a list of all events that must be tracked to stay in compliance with the said profile. You also get a lot of useful information like minimal and recommendation settings, descriptions, and mappings to the ATT&CK matrix. The tool is versatile and it is a must-have for any SoC architect. Make sure to check the tool (Link) and if you have time, contribute to it.
The Glitch In The Matrix
This is hands down my favorite talk so far and that’s mind-blowing because I am far from having enough knowledge on compilers to understand everything that was presented in this talk. Marion is one of those amazing experts who can take a complex topic and present it in an easy to understand format that can be followed by almost everyone. She presented a great overview of compilers, optimizations and she then moved into explaining security issues that result from exploiting compiler optimizations. Her talk gave us all a vivid idea of how dangerous an insecure build pipeline can be and we sure learned a thing or two about GCC.
Hacktivism as a defense technique in a cyberwar
I will refrain from commenting on this talk for multiple reasons but feel free to watch the video recording. Extra points if you can spot my question to the presenter.
DeTT&CT: Mapping your Blue Team to MITRE ATT&CK
This was an informative talk on using the same concepts of the ATT&CK framework from a blue team perspective. The presenters (Marcus Bakker and Ruben Bouman) did a great job and their project looks promising.
Defeating APT10 Compiler-level Obfuscations
The last talk of the day, presented by Takahiro Haruyamaa , a security researcher with mad skills in reverse engineering. He presented part of his work in de-obfuscating the code of ANEL.
Call for Failure (CfF 0x0)
This something new and I have to say, it was a huge success. I truly hope the organizers will keep it in the next edition and all future editions. The idea is simple, people give short talks on failures they lived through and the lessons they learned from these failures. It was a very chill segment of the day and the speakers did an awesome job sharing their failures and many of the lessons they learned. It takes tremendous courage to present your failures to a wide audience but they did it, and they nailed it. We all fail, it’s part of the process towards becoming better.
Power Point Karaoke
Unlike the Call for Failures, powerpoint karaoke isn’t a new thing but it’s definitely close to everyone’s heart. The idea is simple, a punch of people take turns doing presentations to the audience. Too easy, right? Well, you are correct, there are a few interesting twists. First, the presentations are from the internet, they are on random topics. Secondly, speakers pick a number and get a random presentation, they don’t get any information about the presentation before their performance. Thirdly, the person controlling the presentation can skip forward in a fast manner which makes the task much more difficult. Needless to say, this is a brilliant activity, it’s hilarious, and it changes the general mood of the conference from serious security to chill socializing mood which is great if you ask me.
Going Home
By the time PowerPoint karaoke ended, I was exhausted and praying for a bed and some sleep. As soon as the activity was done, I booked a taxi and went to my accommodation. I was thinking of leaving earlier during the day but I am happy I didn’t do that, it was worth the time and energy. It’s 1:00 AM and I am writing with one eye open so I will leave you here. Stay safe.
