It's been a while since I have been to a security conference, and my excitement about moving to Stockholm and the possibilities of attending events was promptly crushed by the two-years-long nightmare known as the COVID-19 pandemic. So, you can imagine my excitement and anticipation for the two most prominent security conferences in Sweden, Security Fest and SEC-T. This post recaps my Security Fest experience and the three days I spent in the beautiful city of Gothenburg.
Conference name: Security Fest
Location: Gothenburg, Sweden
Duration: 2 Days
Dates (This Year): 2-3 June
Ticket price: ca $350 (3500 SEK)
Website: https://securityfest.com/
The Trip
We drove from Stockholm to Gothenburg, or rather my friends drove down to Gothenburg, and they were so nice, they let me tag a long on this mini road trip. The weather was wonderful, and the fields were full of bright colors, not to mention the spectacular views from some of the stops we made along the way. My first road trip in Sweden was a massive success and such a pleasant experience.


Day 1: Thursday
I started the day by getting some breakfast around 7:30 before heading to the venue (few meters away from the hotel lobby) to complete the registration and get my badge and goodies bag. The entire registration process took less than five minutes, and I got a really cool badge (everyone did). The conference was set to start at 9, so we had some time to kill, and we spent it walking around the sponsors area and checking out some of the things they had on display, chatting with some people, and grabbing some cool stickers.
The conference keynote was presented by Jayson E. Street (@jaysonstreet), who spoke about security awareness through the lenses of his work with physical security engagements. Jason is a great presenter, he knows how to capture his audience's attention and how to make his talks enjoyable, and all of that held true for this keynote.
“Humans aren't the weakest part of the link, they are the least invested in.” – Jayson E. Street
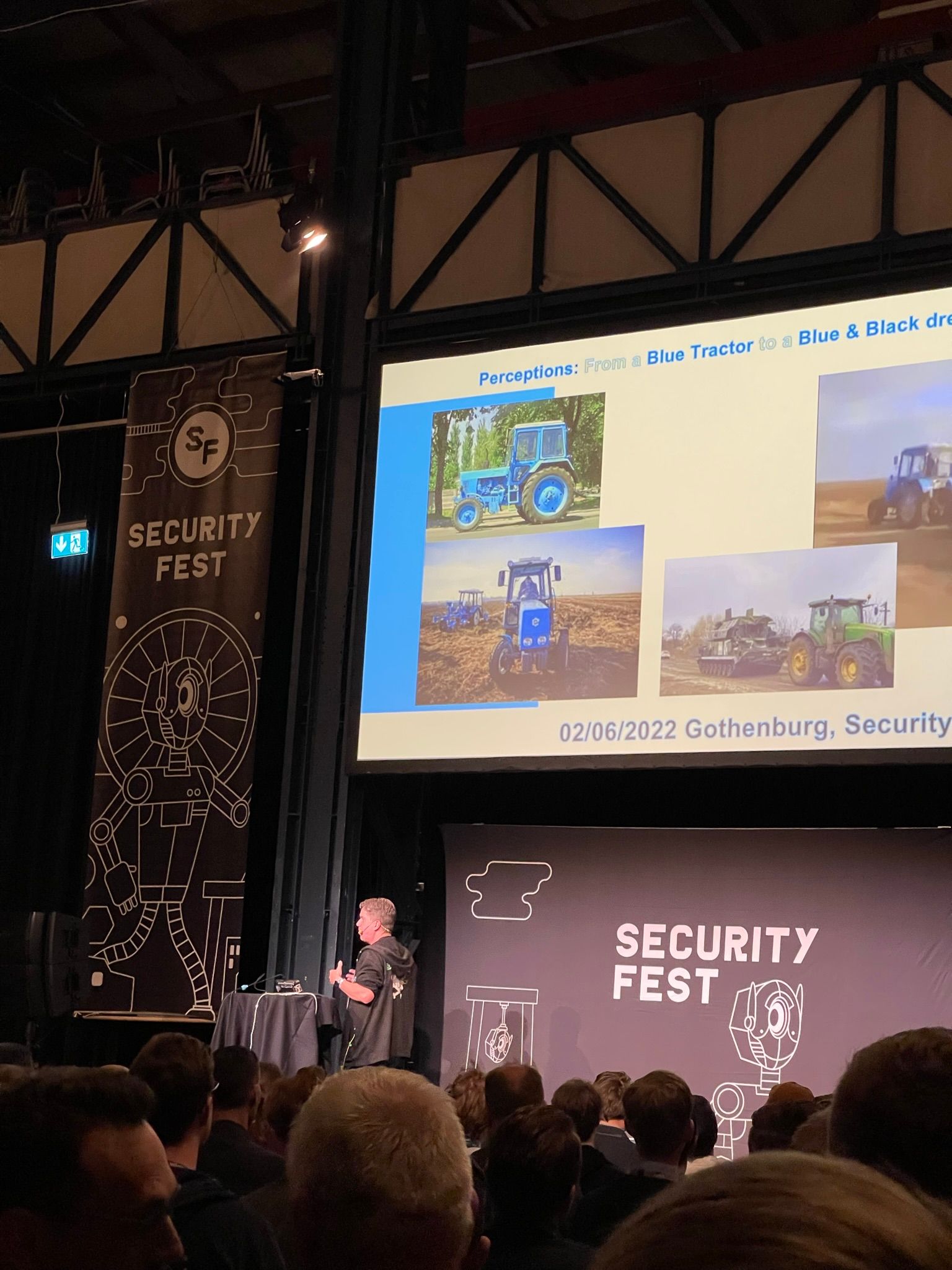


Next up was Dan Tentler (@Viss) who presented a talk titled "Eyes into an active AO during a war". Now, if you know Dan from Twitter, you would know he is really into finding internet-connected things and sharing his interesting findings online. This talk wasn't that much different from many previous talks he did on the topic except for the fact, it was in the context of the Russian invasion of Ukraine this time which made it a rather gloomy and distressing talk, technically interesting nonetheless.

Csaba Fitzl (@theevilbit) was next up on stage where he presented a rather informative talk "10 macOS persistence techniques" during which I learned some interesting information about screen savers, preference panes and other macOS components.
Abraham Aranguren took the stage next and presented his talk, Hacking JavaScript Desktop apps with XSS and RCE which was very interesting considering how many desktop apps nowadays are basically Electron applications that can be vulnerable to the same security vulnerabilities affecting traditional web applications. I must say, he went through the slides really fast and for a moment, I struggled to keep up, but I will for sure watch the recording to make sure I catch all the useful information he was sharing.

At the point (around 14:20), I felt really exhausted so – and I am ashamed to say this – I skipped the next talk on the schedule, How I got remote root shell on a Helium crypto miner presented by Mikael Falkvidd (@mfalkvidd), and went up to my hotel room for a quick nap. I will definitely watch the recording to catch up on what I missed, and so should you (if you didn't watch it live).
I made it back in time for the Pwned in Space talk by Paul P Coggin (@PaulCoggin) in which he talked about the insecurity of satellites, the lacking regulations and agreements on cybersecurity in space, while also sharing some fascinating stories of cyber intrusions affecting satellites. It's terrifying to think of how insecure these things orbiting our planet are, definitely inspired me to do more reading on the topic.
The last talk of the day was How to write a BANGER blogpost! (Hacking the Google algorithm) by Fredrik "STÖK" Alexandersson (@stokfredrik), and it was hands down my favorite talk in this edition of Security Fest, which is even more impressive considering it wasn't about cutting-edge security research or some peculiar vulnerability. Fredrik talked about the importance of SEO and proper crafting of posts and online content to ensure greater reach for whatever content you are publishing. Many of the things he talked about are things I barely think about when writing blog posts, so it was an eye-opener and a great learning experience.

With all the talks for the first day done, it was time for dinner but before that, we had a short break to mingle and grab some water while everything is prepared in the dinner room. The next few hours were spent on having dinner, watching people play a rather difficult quiz, and enjoying a live band play a wonderful selection of songs.

Day 2: Friday
I couldn't sleep for long the night before, so I decided to watch the talks of the second day from my room (using the live stream) and go down when I feel more rested (never happened :(). This is also why I have no photo from the second day except for some screenshots I took from the live feed, so this will be much shorter than my recap for the first day.
The first talk of the day was "I know what your 'Microsoft Mainframe' did last summer!" by Yossi Sassi (@Yossi_Sassi) who talked about doing forensics investigations in an AD activity. Before jumping into the forensics, Yossi offered a brief intro to the security problems plaguing Active Directory, and the prevalent exploitation of AD during both testing engagements and malicious attacks. The rest of the talk was very informative, with numerous hands on demonstrations, including one of a new tool for detection of suspicious Kerberos golden tickets.
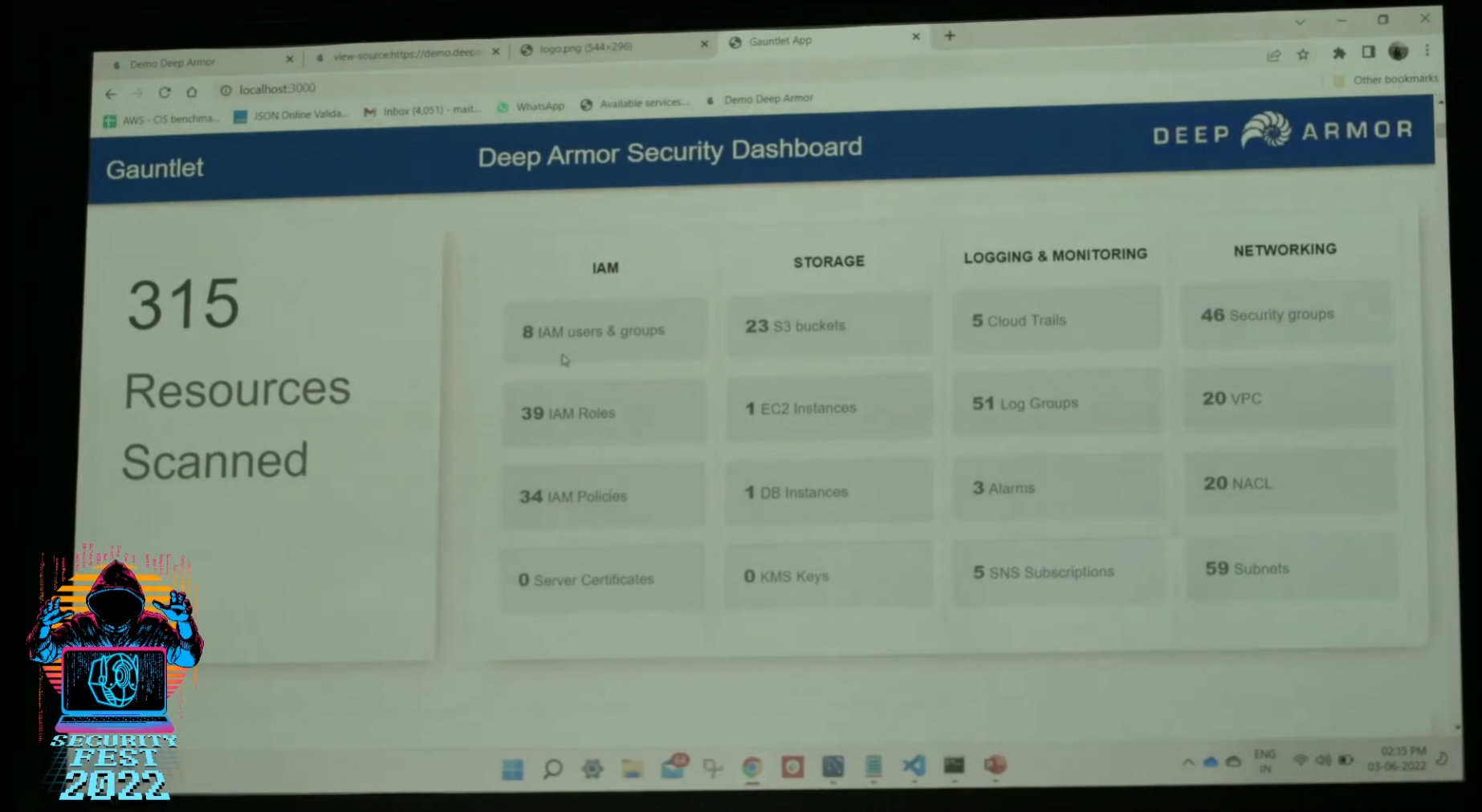
Next on stage was Maithri Nadig and Krishnaa Srinivasa presenting their talk "Exploitation and automated detection of threats to modern cloud infrastructure" in which they went through some basics of cloud security, touched on the CIS benchmarks available for cloud providers (e.g. Azure, AWS), and discussed some common cloud attacks and security misconfigurations that can lead data breaches –among other consequences–. They also demonstrated their new tool that allows AWS customers to scan their cloud environment for security misconfigurations (currently scans for 60+ misconfigurations).
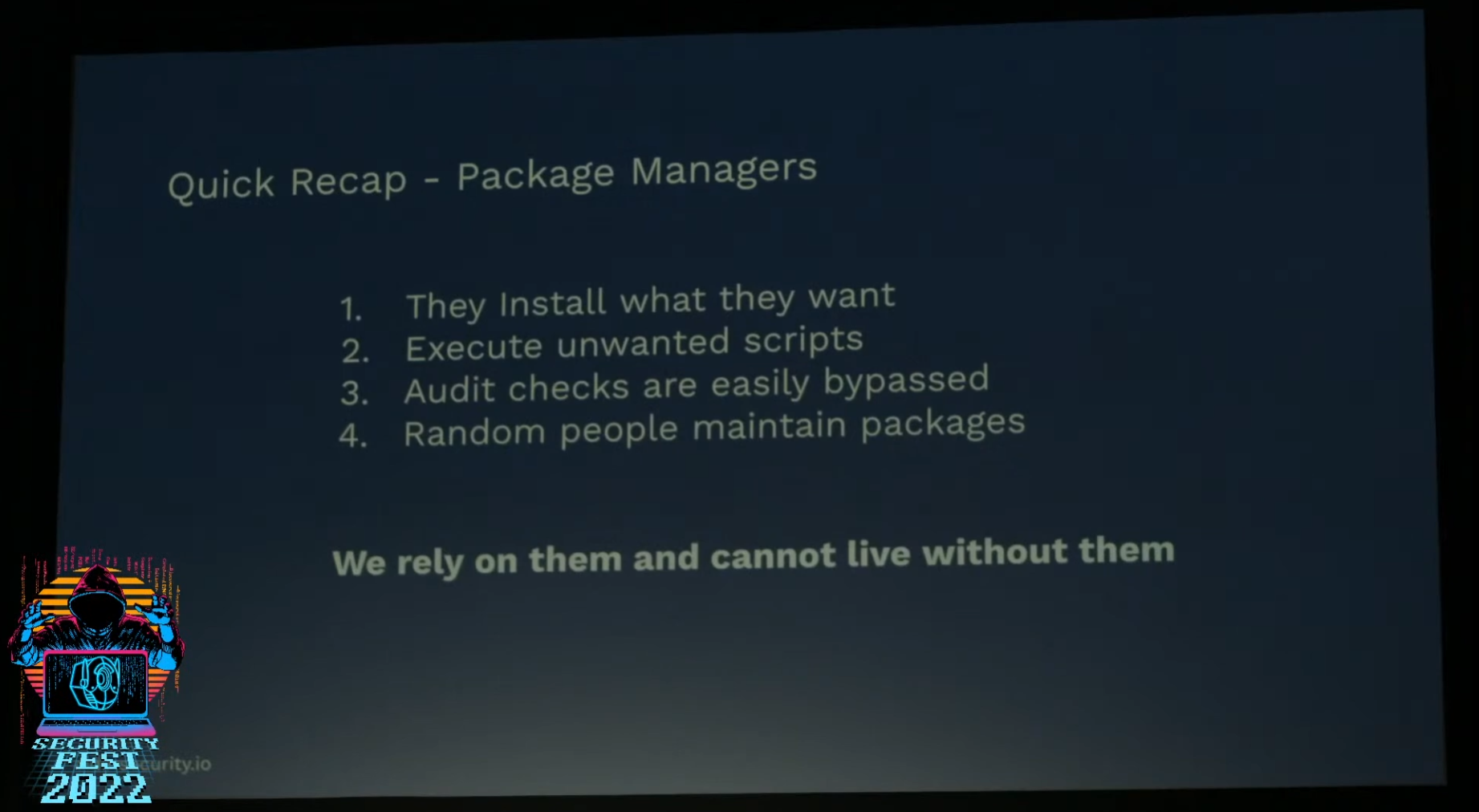
Rotem Bar (@rotembar) took the stage next and delivered his talk, "Do you trust your package manager?" Malicious packages have been all over the news recently, and compromises of supply chains for packages is becoming a real headache, Rotem explained many of the issues with the npm package manager and how some of these can be abused by attackers, he then offered some good advice on how to avoid falling for these attacks and improve your internal security when it comes to using third-party packages and package managers.
And, the last talk of the day was Hacking Network APIs by Dan Nagle. I missed this one entirely because I was having a fantastic lunch with my friend in one of the best fish restaurants in Sweden. This also means I didn't attend or watch the panel (nicely titled Wrong answers only), the CTF awards or the wrap up of the conference.

Once I was done with my lunch, my friends picked me from the restaurant, and we set off on our way back to Stockholm. The views were just as amazing, but the weather was a bit moody and for a couple of minutes, we got some rain. We made a couple of stops, including one to have a quick meal in what is now one of my favorite restaurants, ChopChop Asian Express.

Was It Worth It?
100%. I can't recommend this conference enough. Good talks, super friendly community, great discussions, good food, wonderful entertainment, and Gothenburg is one hell of a city to visit with so much to offer. If you haven't been to Security Fest before (or if you had), I hope to see you there next year.
Links
- https://securityfest.com/
- https://securityfest.com/schedule/
- https://github.com/YossiSassi/hAcKtive-Directory-Forensics


