Oauth Proxy is a reverse proxy and static file server that provides authentication using Providers (Google, GitHub, and others) to validate accounts by email, domain or group.
Requirements
- You need a website running on Nginx.
- You need an authentication source that supports Oauth (GSuite, Github, ...)
- You need SSH access to your server.
- You need basic knowledge of Linux and Web Servers.
Instructions
SSH into the server hosting the web application.
Download the latest version of OAUTH Proxy
wget https://github.com/pusher/oauth2_proxy/releases/download/v5.0.0/oauth2_p roxy-v5.0.0.linux-amd64.go1.13.6.tar.gzCreate a directory /opt/oauth2_proxy
sudo mkdir /opt/oauth2_proxyMove oauth2_proxy to the directory created above
sudo mv oauth2_proxy /opt/oauth2_proxyCreate a new configuration file (oauth2_proxy.cfg)
cd /opt/oauth2_proxy
sudo touch oauth2_proxy.cfg
sudo nano oauth2_proxy.cfgCopy the following configuration to the file you just created (swap the masked values with your own)
upstreams = [
"http://127.0.0.1:8080/" ]
# Email Domains to allow authentication for (this authorizes any email on this domain). To authorize any email addresses use "*"
email_domains = [ "example.com" ]
# The OAuth Client ID, Secret
client_id = "*************************************"
client_secret = "***********************************"
#Cookie Settings
cookie_secret = "***********************************"
# cookie_domain = ""
# cookie_expire = "168h"
# cookie_refresh = ""
# cookie_secure = true
# cookie_httponly = trueAdjust the configuration parameters for your particular server and web application.
Create a new systemd service for oauth_proxy
sudo touch /etc/systemd/system/oauth_proxy.service
sudo nano /etc/systemd/system/oauth_proxy.serviceCopy the following systemd service configuration to the service configuration file you just created
# Systemd service file for oauth2_proxy daemon
[Unit]
Description=oauth2_proxy daemon service
After=syslog.target network.target
[Service]
# www-data group and user need to be created before using these lines User=www-data
Group=www-data
ExecStart=/opt/oauth2_proxy/oauth2_proxy -config=/opt/oauth2_proxy/oauth2_proxy.cfg
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process
Restart=always
[Install]
WantedBy=multi-user.targetEnable and start the service
sudo systemctl daemon-reload
sudo systemctl enable oauth_proxy.service
sudo systemctl start oauth_proxy.serviceMake a backup of the current Nginx configuration file at /etc/nginx/site-available/*
cd /etc/nginx/site-available/
sudo cp <configfilename> <configfilename>.backupOverride the Nginx configuration with the following configuration
pwd # confirm you are working inside sites-available
sudo rm <configfilename>
sudo nano <configfilename>server {
listen 80;
listen [::]:80;
server_name <(sub)domain>;
location /oauth2/ {
proxy_pass http://127.0.0.1:4180;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Scheme $scheme;
proxy_set_header X-Auth-Request-Redirect $request_uri;
}
location / {
auth_request /oauth2/auth;
error_page 401 = /oauth2/sign_in;
# pass information via X-User and X-Email headers to backend
# requires running with --set-xauthrequest flag auth_request_set $user $upstream_http_x_auth_request_user;
auth_request_set $email $upstream_http_x_auth_request_email;
proxy_set_header X-User $user;
proxy_set_header X-Email $email;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_pass_header Server;
proxy_connect_timeout 3s;
proxy_read_timeout 10s;
# if you enabled --cookie-refresh, this is needed for it to work with auth_request
auth_request_set $auth_cookie $upstream_http_set_cookie; add_header Set-Cookie $auth_cookie;
proxy_pass http://127.0.0.1:8080;
}
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/<(sub)domain>/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/<(sub)domain>/privkey.pem;
include /etc/letsencrypt/options-ssl-nginx.conf;
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem;
if ($scheme != "https") {
return 301 https://$host$request_uri;
}
}Important Notes
- Adjust the Nginx configuration parameters to suit your server and web application.
- Ensure the domain you are using is part of the callback domains list in your GSuite OAUTH application
Reload Nginx.
sudo systemctl reload nginx.serviceBrowser to your website address
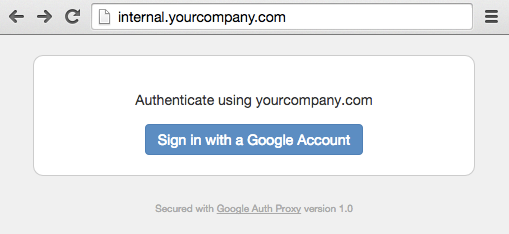
Use your browser of choice to navigate to the website URL, you should be greeted by the following screen: