My home network always had a simple security setup, a router, a firewall, and a bunch of computers, that's it. That setup works great and doesn't hit my productivity in any noticeable way, but it can be improved and after months of ignoring it, I finally got around to reviewing the setup and making some improvements.
Setting Up The Firewall
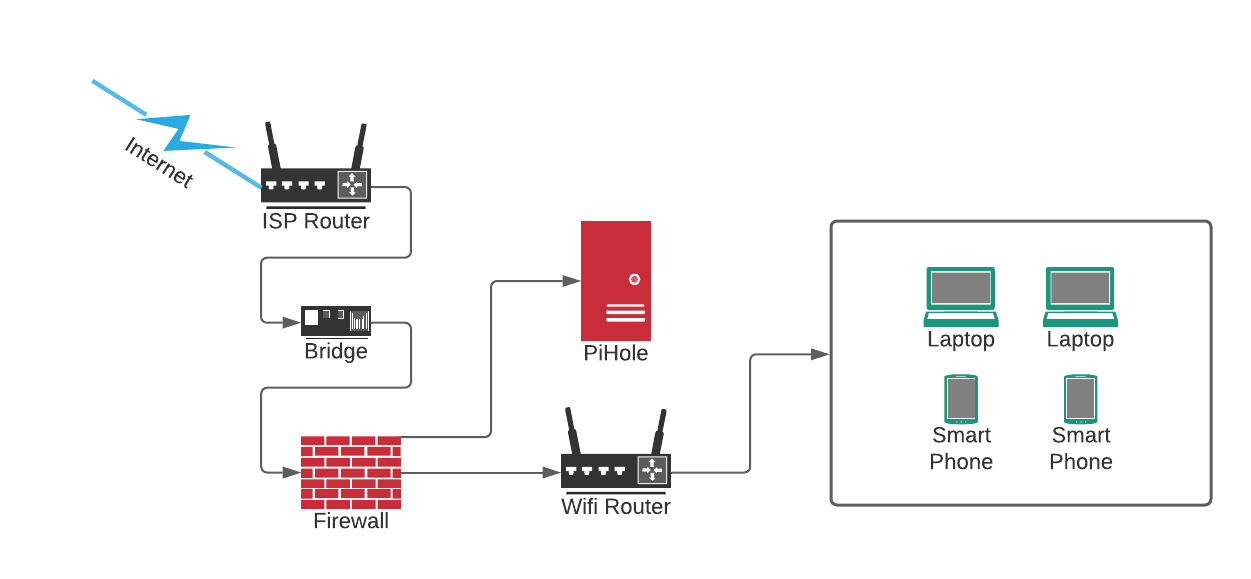
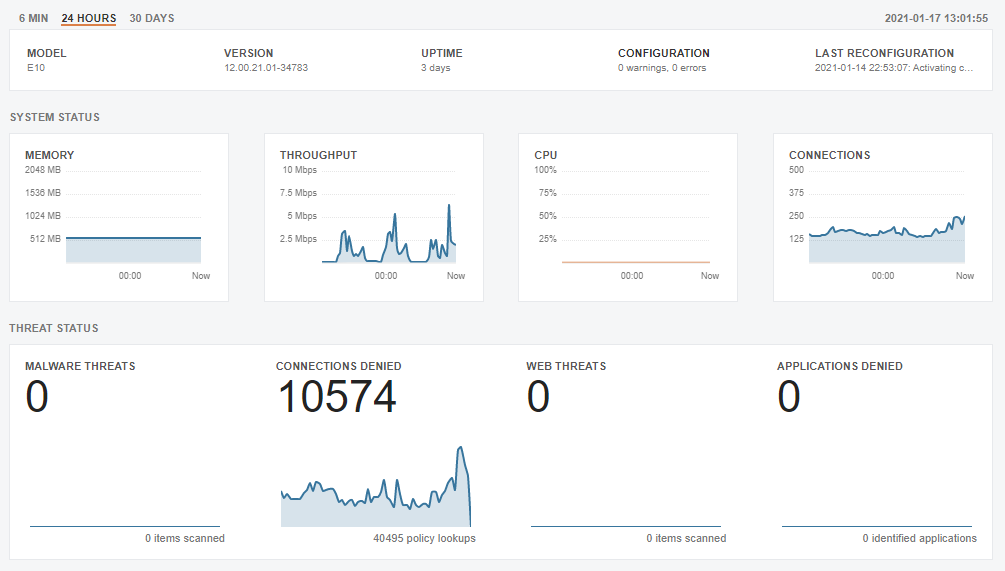
I have a nice firewall that I got from my previous employer who specializes in building network security products. I had it configured in my previous home but since I moved a few months ago I forgot to configure it in my new home, until this past week.
The Clavister E10 is the perfect entry-level next-generation security appliances, built to deliver comprehensive and powerful enterprise-grade firewall services (Source).
Setting up the firewall itself was easy-peasy, getting the ISP router to work nicely with the firewall was a much harder task. The cable from the wall to the ISP router is a coax cable, so I don't have many options other than keeping the ISP router and putting it in bridge mode, so the traffic is routed to the firewall instead of it being processed by the router.
Setting Up PiHole
I bought a new Raspberry Pi when I was visiting Luleå on new years, but I didn't get to unpack it until later past week. I simply installed PiHole on it and configured my firewall to use it as a DNS resolver which forced my entire network to go through it for any DNS queries.
Pi-hole is a Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole and optionally a DHCP server, intended for use on a private network (Source).
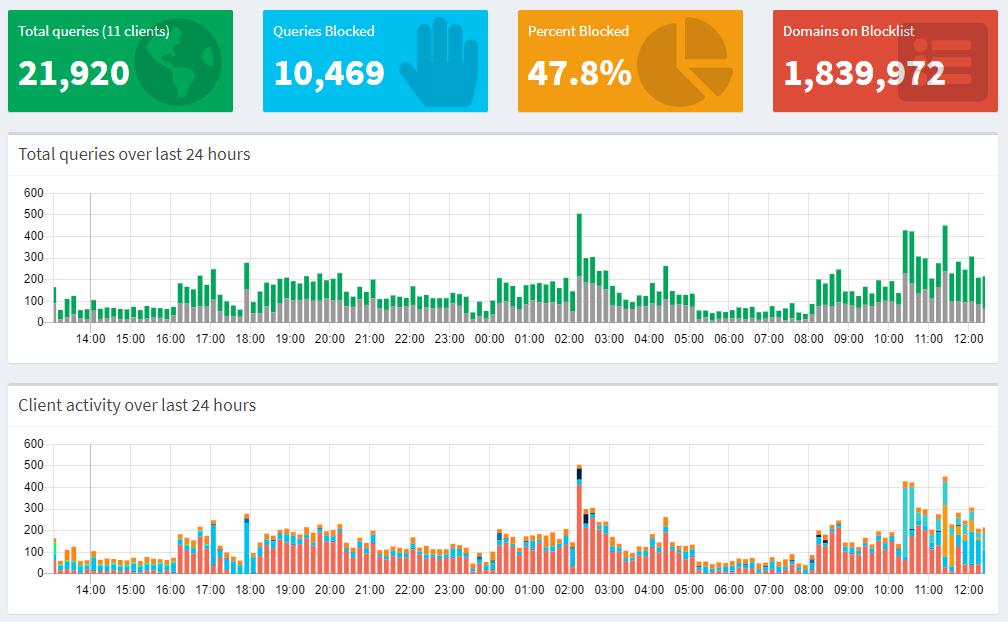
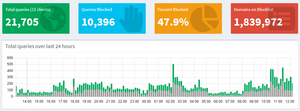
PiHole comes with a default list or URLs that are blocked, but while browsing Twitter, I saw this tweet from Scott Helme which made me up the ante a little and now the list of blocked domains include around 1.8 million URLs.
I recently added several new hosts lists to my @The_Pi_Hole, taking my blocked domains to 1.8m+! Over 20% of DNS queries on my network are now blocked and I have literally a few exceptions to make stuff work. pic.twitter.com/PRN1s8PoaX
— Scott Helme (@Scott_Helme) January 13, 2021
Setting Up TailScale
Now that I have PiHole up and running, I realized I am once again back at the problem of remote access to both the PiHole and my Jellyfin server. I would usually configure a VPN on the firewall and use it, but I found out about TailScale and my mind was blown away with the simplicity and ease of use, so I had to give it a try.
Zero config VPN. Installs on any device in minutes, manages firewall rules for you, and works from anywhere. (Source)
There are two reasons I need TailScale, those are:
- To keep the PiHole protection while on the go.
- To access my laptops and Jellyfin server while on the go.
Eventually, I will configure a VPN on my firewall but for now, TailScale it is.
Next Steps
Now that I have everything in place, I have a couple of ideas for the near future:
- Ship logs from the firewall to an ELK instance and do more in-depth analysis of my network traffic.
- Build a script to ship important indicators from the firewall and PiHole logs to a MISP instance.
- Write a recap post in December to review traffic trends and interesting observations.